Web App Security
Learning tips, automation, OSINT, SOC fundamentals, and web penetration testing (XSS, SQL injection, CSRF) with ethical, permission-based practice.
Black Aesthetic · White Ethics · MultiHAT in Training
CSE student at AIUB, web developer, and cybersecurity enthusiast. I learn by building secure systems, testing web apps, and sharing knowledge openly. Sagar Biswas is focused on MultiHAT-in-Training Web App Security and Development.
COMMUNITY
· AIUB
· GitHub
· MutliHAT - YT
· AIUB CyberSecurity & Programming Society - Facebook Community Group

$ whoami
sagarbiswas-multihat
$ mission --current
learn. build. secure.
$ status --op
student · builder · ethical
I am a Computer Science and Engineering (CSE) student at American International University–Bangladesh (AIUB). I focus on web development, web application security, and building modern web experiences. My goal is to become a true MultiHAT who can both attack and defend with integrity.
Learning tips, automation, OSINT, SOC fundamentals, and web penetration testing (XSS, SQL injection, CSRF) with ethical, permission-based practice.
Building clean, efficient applications with HTML, CSS, JavaScript, PHP, and React, and focusing on secure-by-design architecture.
Active in cybersecurity learning platforms and community work, sharing resources and open-source tools with the AIUB Cybersecurity & Programming Society.
Hands-on learning tracks and the skills I’m growing every day.
Open-source work and learning assets from my GitHub.
A beginner-friendly guide to networking fundamentals, breaking down how the internet really works. Covers TCP vs UDP, IP addressing, DNS, OSI & TCP/IP models, IPv4 vs IPv6, and Wi-Fi security basics. Perfect for students and tech enthusiasts building strong networking foundations.
View: Networking Notebook (AIUB Cybersecurity & Programming Society) NotebookFrom my first echo "Hello World" to real-world automation, this Bash Scripting Handbook documents my complete learning journey—covering core concepts, scripting logic, debugging, security, and practical projects. A hands-on roadmap for mastering Bash and Linux automation. 🐧⚙️
View: Bash Script Handbook (AIUB Cybersecurity & Programming Society) NotebookAn intermediate-to-advanced handbook focused on using Python for real-world cybersecurity. Covers automation, secure coding, powerful libraries, and hands-on ethical hacking projects. Built for learners who want practical skills, not just theory.
View: Python for Cybersecurity Handbook (AIUB Cybersecurity & Programming Society) NotebookNOTE: To find more notebooks, projects, tips and tricks like this, join my Facebook community group and check the featured section for notebooks and explore the Posts to discover real-world projects.
Educational use only: The tools and notebooks listed here are for learning, research, and defensive purposes only. Do not use them for malicious activity. Contact me for responsible disclosure or questions.
A simple educational web vulnerability scanner that crawls a site and checks for open directories, missing security headers, and basic SQLi/XSS patterns. Supports multithreaded crawling, insecure cookie detection, method enumeration, and detailed logging. Outputs results to scan_report.json and logs all activity in scanner.log.
View repo: Web Vulnerability Scanner ToolingThis repository contains a virtual assistant named "Sagar," tailored for CSE students passionate about cybersecurity. It processes commands to open websites, play music, or respond via an AI model. The assistant supports both single-line and multi-line inputs, offering a practical tool for learning and task automation.
View repo: A Pythonic Hackathon CyberSecurity AssistantSharpLink is a simple URL shortener web app built with Flask. It lets you create short links from long URLs, choose custom aliases, set expiration dates, and optionally generate TinyURL mirrors. Links are stored locally in JSON and redirect instantly. Includes copy buttons, expiry handling, and is easy to run locally or deploy online.
View repo: SharpLink URL Shortener Web DevPython-based keylogger for ethical use, capturing keystrokes and emailing logs. Features include retry logic for email delivery, log file management, and cross-platform support (Windows/Linux). Configurable for auto-start via systemd or Startup folder. Designed for educational purposes, penetration testing with consent, and self-monitoring.
View repo: A Pythonic Keylogger CyberSecurityThis Python script creates a voice-controlled virtual assistant using speech recognition, AI responses, and text-to-speech conversion. It listens for commands like opening websites or playing music, processes them using AI, and responds via speech. Powered by Google’s Speech Recognition, Groq API, and pyttsx3 for voice interaction.
View repo: Speech-to-Speech AI Assistant AIA desktop Library Management System built with Python and Tkinter. Manage books, members, checkouts, returns, and overdue items with automatic local saving. Features search, filters, analytics, CSV/JSON export, and backups. Includes secure login with SHA-256 password hashing and TOTP-based two-step authentication. Runs fully offline on Windows.
View repo: Library Management System AITIP: For more notebooks, projects, and real-world tips, join my Facebook community group and check the featured section along with recent posts.
Threat stories, security lessons, and real-world awareness topics.

A notebook‑style guide with exact commands, recommended prompt answers, screenshots, and fixes. Perfect for a clean Windows + WSL2 + Kali GUI setup.
Read the blog: WSL2 + Kali Linux + Win‑KeX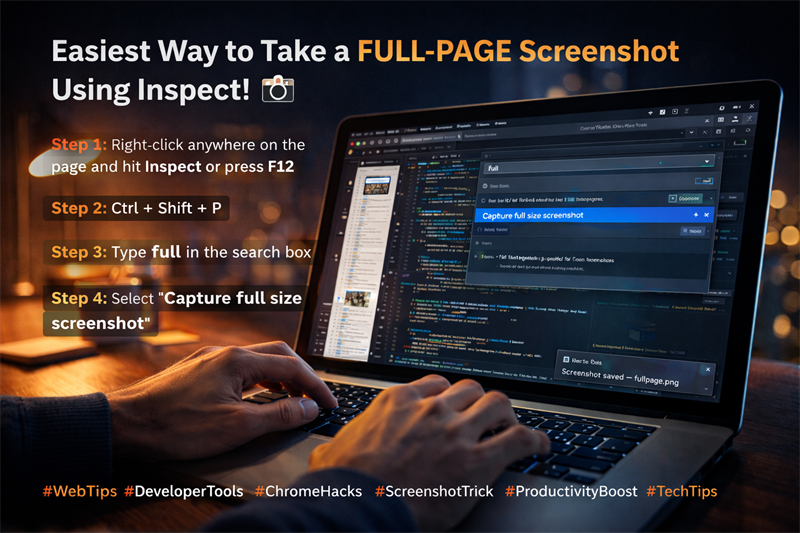
Open DevTools, use the Command Menu, and capture a full‑size screenshot in seconds. No extensions needed.
Read the blog: Full-page screenshot using Inspect
Printers are often ignored, under-patched, and trusted by everything inside a network. This post breaks down how a printer became the quiet entry point for attackers — and what you can do to stop it.
Read the blog: Printer attack entry point
AI দিয়ে দ্রুত ডেলিভারি সম্ভব, কিন্তু ভুল সিদ্ধান্তে তৈরি হয় বাড়তি জটিলতা। এই লেখায় আছে সহজ ব্যাখ্যা — কোথায় স্পিড দরকার, আর কোথায় সরলতা দরকার।
Read the blog: Vibe coding & tech debt
Nation-state actors can correlate metadata and behavior. VPNs and proxies help, but real anonymity depends on identity separation, fewer actions, and avoiding linking accounts.
Read the blog: Anonymity & OpSec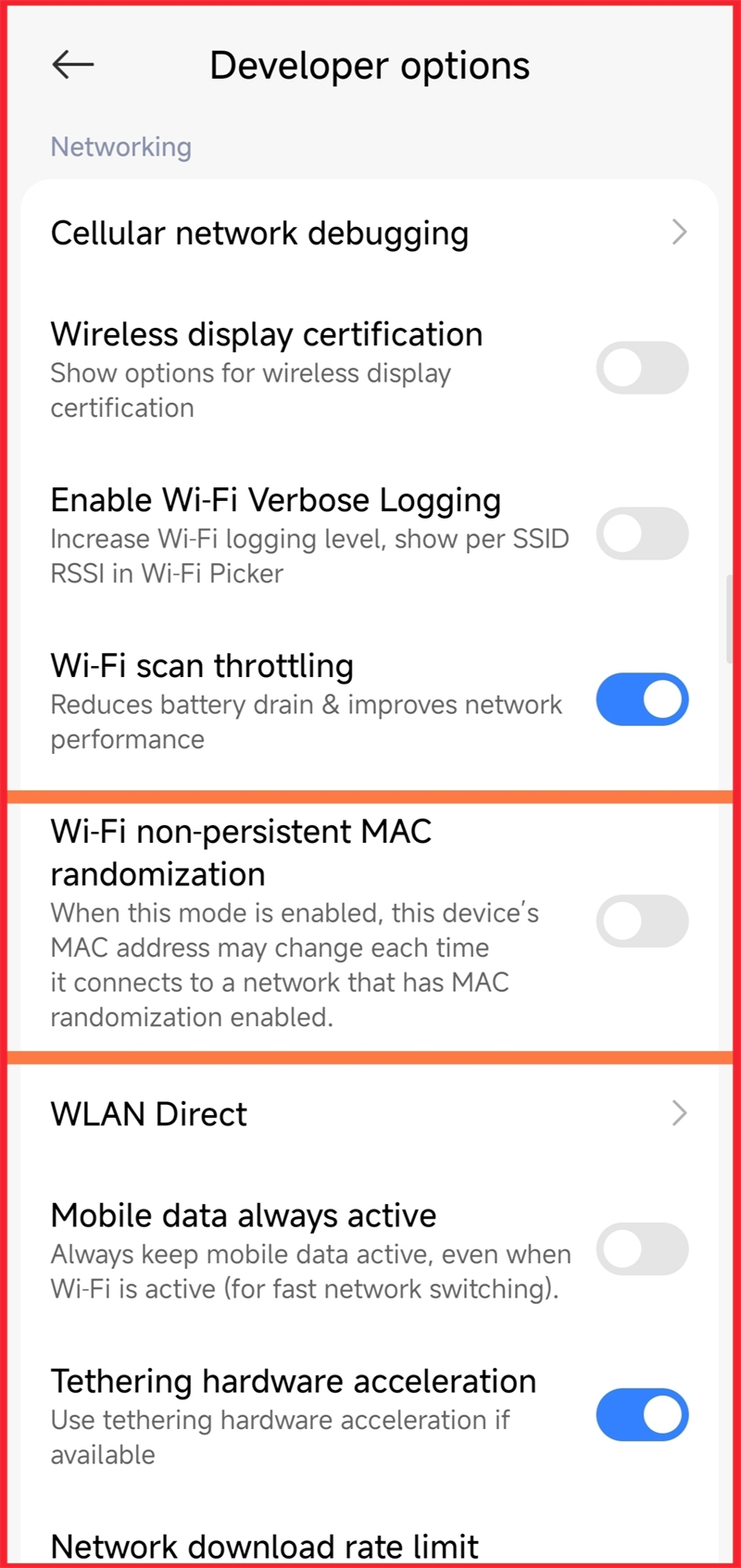
Blocking by MAC can be bypassed on modern phones. The safest fix is a password change plus tighter router settings.
Read the blog: Wi-Fi security alert
Quantum computers threaten current RSA and ECC encryption. NIST's post-quantum standards exist today. Learn what organizations should do now.
Read the blog: Quantum cryptographyVerified learning milestones and professional training.
_page.jpg)

Download or view my latest resume.
Videos, learning labs, and community resources I follow and contribute to.
Watch my featured video on YouTube for updates and walkthroughs.
Watch videoAnother featured focused on security learning and tooling.
Visit the communityPortSwigger, OWASP Top 10, TryHackMe, and Hack The Box.
Explore labsOpen to ethical collaboration, learning opportunities, and community projects.
Bangladesh · Remote collaboration
Currently focused on learning and open-source
Responsible disclosure only. If you discover a security issue in my work, contact me directly at eng.sagar.aiub@gmail.com.