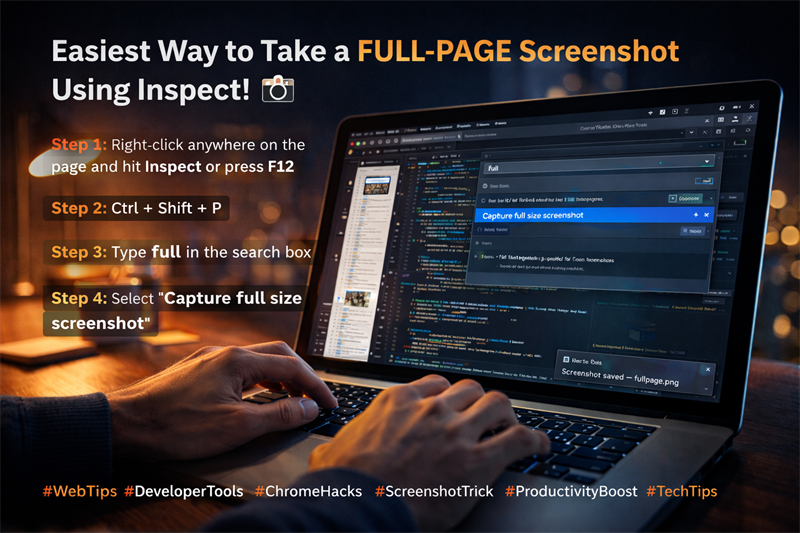
WSL2 + Kali Linux + Win‑KeX (GUI) Installation Guide (Beginner‑Friendly)
A notebook‑style guide with exact commands, recommended prompt answers, screenshots, and fixes. Built for beginners who want a clean WSL2 + Kali + Win‑KeX setup on Windows.
Read the blog